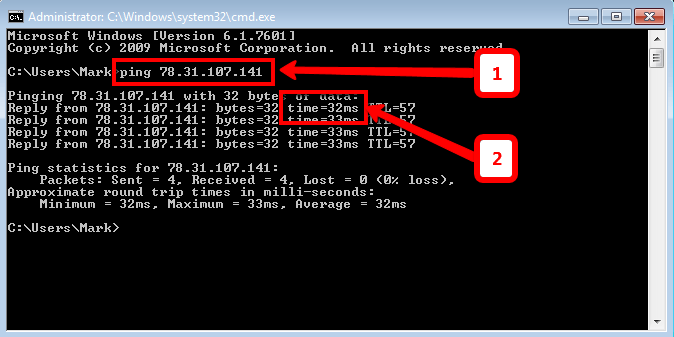
The third module was all to do with both the transport and the application layers of networking and the learning objectives were as follows:
- To describe TCP ports and sockets
- To examine the different components of a TCP header
- To compare differences between connection-oriented and connectionless protocols
- To explain how TCP is used to ensure data integrity
So first off I began with the transport layer, learning about the importance of multiplexing and demultiplexing and how ports use it to direct traffic to specific services or servers on the network e.g. port 80 is commonly used for http web servers.
Next I dissected a TCP segment, looking at the various fields that make up a TCP header and understanding how they use certain control flags such as SYN and ACK in order to establish a connection using the '3 way handshake'.
I learnt about sockets, the various states they can be in and how this information can aid in troubleshooting socket issues before also learning the difference between TCP and UDP as connection-oriented and connectionless protocols. Finally, I had a brief mention of firewalls and how they block IP addresses from accessing certain ports to ensure security.
After covering the transport layer it was on to the application layer, understanding that the data payload of a TCP segment contains all the data an application is wanting to send or receive. I learnt that unlike the other network layers that operate with only one or two protocols, when it comes to the application layer there are a wide number of different protocols, such as HTTP for web services, that allow all applications to have interoperability. To round this off I touched on the OSI model of networking, learning the key difference is the addition of another two layers, session and presentation.
This module was fairly short and straight forward really, especially in comparison with learning what goes on at the network layer. On the whole, I've enjoyed beginning to imagine networking as a 5 layer model and I think it's quite helpful breaking it down in this way to understand the inner workings that are happening at each layer. On to the next module which will cover a variety of networking services and how they are utilised.
Dave